dnscrypt.pl DNSSEC Outage: 2021-02-09 to 2021-02-11
Date: February 10, 2021
Overview
This page gives some details on the dnscrypt.pl DNSSEC outage on February 10, 2021. This is at least the 9th DNSSEC outage for dnscrypt.pl. Please note: DNSCrypt itself is not a DNSSEC protocol and is safe to use. DNSCrypt encrypts DNS queries while DNSSEC doesn't encrypt DNS queries.
Timeline / DNSViz
- 2021-02-09 17:47:51 UTC — RRSIGs expire
- 2021-02-10 17:59:42 UTC — Expired RRSIGs
- 2021-02-10 18:06:33 UTC — Expired RRSIGs
- 2021-02-11 17:06:46 UTC — Expired RRSIGs
Here is a mirror which shows the outage in DNSViz, courtesy of archive.is.
DNSSEC Debugger
Unlike DNSViz, Verisign's DNSSEC Debugger doesn't archive results, so here's a screenshot of my web browser's output from February 10, 2021:
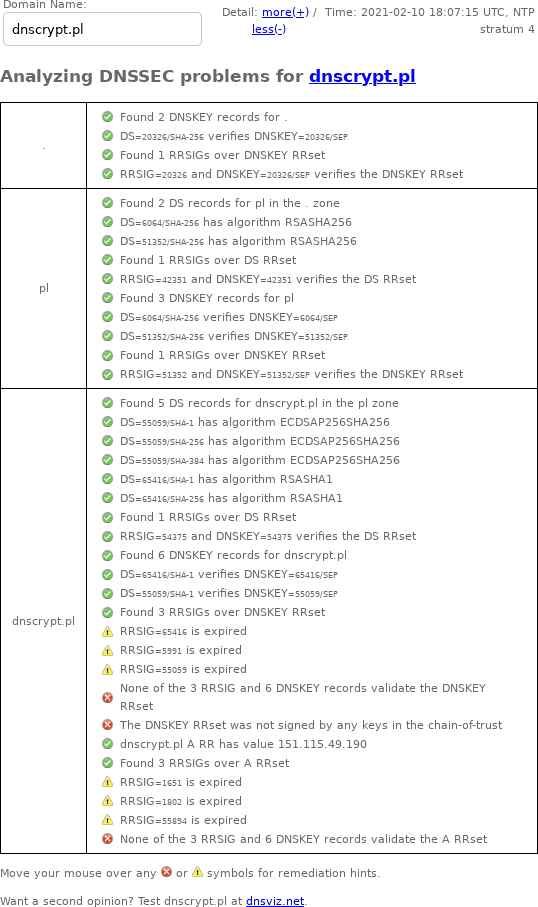
There's an archive.is copy of this data. Additionally there's a copy from archive.org.
Zonemaster
- zonemaster.net archived expired RRSIG errors. (archive.is copy)
- zonemaster.labs.nic.cz archived expired RRSIG errors. (archive.is copy)
- zonemaster.iis.se archived expired RRSIG errors (archive.is copy)
Google Public DNS, with and without DNSSEC
With DNSSEC enabled, queries fail:
$ dig +dnssec a dnscrypt.pl. @8.8.8.8.
; <<>> dig 9.10.8-P1 <<>> +dnssec a dnscrypt.pl. @8.8.8.8.
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 50789
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 512
;; QUESTION SECTION:
;dnscrypt.pl. IN A
;; Query time: 591 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Wed Feb 10 18:01:16 UTC 2021
;; MSG SIZE rcvd: 40
You have to disable DNSSEC to make DNS work:
$ dig +cd a dnscrypt.pl. @8.8.8.8.
; <<>> dig 9.10.8-P1 <<>> +cd a dnscrypt.pl. @8.8.8.8.
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 21005
;; flags: qr rd ra cd; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;dnscrypt.pl. IN A
;; ANSWER SECTION:
dnscrypt.pl. 3599 IN A 151.115.49.190
;; Query time: 179 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Wed Feb 10 18:01:16 UTC 2021
;; MSG SIZE rcvd: 56
drill trace
Since DNSSEC contains so much garbage, I put the complete drill trace into its own file, with the relevant portion below (emphasis added):
;; Domain: dnscrypt.pl.
[B] dnscrypt.pl. 86400 IN DNSKEY 256 3 5 ;{id = 1651 (zsk), size = 1024b}
dnscrypt.pl. 86400 IN DNSKEY 256 3 13 ;{id = 55894 (zsk), size = 256b}
dnscrypt.pl. 86400 IN DNSKEY 257 3 7 ;{id = 5991 (ksk), size = 2048b}
dnscrypt.pl. 86400 IN DNSKEY 257 3 5 ;{id = 65416 (ksk), size = 2048b}
dnscrypt.pl. 86400 IN DNSKEY 257 3 13 ;{id = 55059 (ksk), size = 256b}
dnscrypt.pl. 86400 IN DNSKEY 256 3 7 ;{id = 1802 (zsk), size = 1024b}
[B] dnscrypt.pl. 3600 IN A 151.115.49.190
;; Error: No keys with the keytag and algorithm from the RRSIG found
;;[S] self sig OK; [B] bogus; [T] trusted
Logfile examples
- [1612979583] unbound[5689:0] info: validation failure <www.dnscrypt.pl. A IN>: No DNSKEY record from 79.98.145.34 and 193.70.13.218 and 79.98.145.34 and 193.70.13.218 and 193.70.13.218 and 79.98.145.34 and 193.70.13.218 and 79.98.145.34 and 193.70.13.218 and 193.70.13.218 and 193.70.13.218 and 193.70.13.218 and 193.70.13.218 and 193.70.13.218 and 193.70.13.218 and 79.98.145.34 and 193.70.13.218 and 193.70.13.218 and 193.70.13.218 and 79.98.145.34 and 193.70.13.218 and 79.98.145.34 and 193.70.13.218 and 193.70.13.218 and 79.98.145.34 and 193.70.13.218 and 193.70.13.218 and 79.98.145.34 and 193.70.13.218 and 79.98.145.34 and 193.70.13.218 and 193.70.13.218 and 79.98.145.34 for key dnscrypt.pl. while building chain of trust
- [1613069436] unbound[5689:0] info: validation failure <www.dnscrypt.pl. A IN>: No DNSKEY record from 193.70.13.218 and 193.70.13.218 and 79.98.145.34 and 193.70.13.218 and 193.70.13.218 and 193.70.13.218 and 79.98.145.34 and 79.98.145.34 and 193.70.13.218 and 79.98.145.34 and 193.70.13.218 and 79.98.145.34 and 193.70.13.218 and 193.70.13.218 and 79.98.145.34 and 193.70.13.218 and 193.70.13.218 and 193.70.13.218 and 193.70.13.218 and 79.98.145.34 and 79.98.145.34 and 79.98.145.34 and 193.70.13.218 and 79.98.145.34 and 79.98.145.34 and 193.70.13.218 and 79.98.145.34 and 79.98.145.34 and 193.70.13.218 and 79.98.145.34 and 79.98.145.34 and 79.98.145.34 and 79.98.145.34 for key dnscrypt.pl. while building chain of trust
Just want to note what an ugly protocol DNSSEC is. Even the logs are heinous.
