.xn--mgbbh1a TLD DNSSEC Outage: 2020-01-01 to 2020-01-07
Start Date: January 1, 2020
Overview
This page gives some details on the .xn--mgbbh1a TLD DNSSEC outage from January 1 to January 7, 2020. This is an IDN TLD.
Timeline / DNSViz
(At the time of this writing, DNSViz historical archives have been down for about a year. DNSSEC makes its users think downtime doesn't matter.)
- 2020-01-01 23:16:18 UTC — first personally observed xn--mgbbh1a DNSSEC failure
- 2020-01-07 13:02:47 UTC — last personally observed xn--mgbbh1a DNSSEC failure
Here's a screenshot, since DNSViz no longer archives outages:

Thankfully, archive.is made a copy of the DNSViz output.
DNSSEC Debugger
Here's a screenshot of my web browser's output from January 2, 2020:
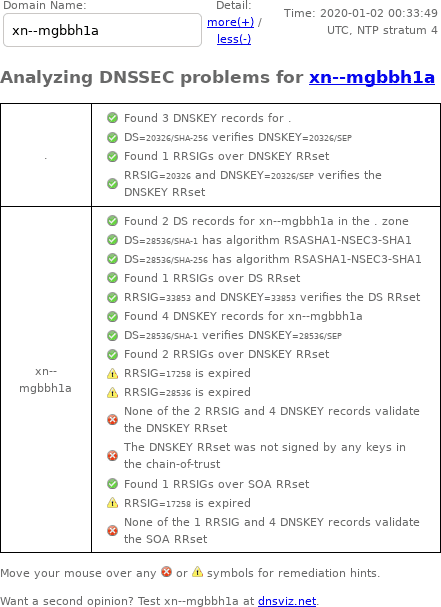
There's an archive of the DNSSEC Debugger output provided by archive.is.
Google DNS: with and without DNSSEC
DNSSEC can be disabled in queries via the CD (checking disabled) bit. Let's compare DNS queries with and without DNSSEC.
$ dig +dnssec ns xn--mgbbh1a. @8.8.8.8
; <<>> DiG 9.4.2-P2 <<>> +dnssec ns xn--mgbbh1a. @8.8.8.8
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 29331
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 512
;; QUESTION SECTION:
;xn--mgbbh1a. IN NS
;; Query time: 33 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Wed Jan 1 23:16:22 2020
;; MSG SIZE rcvd: 40
You have to disable DNSSEC to make DNS queries work:
$ dig +cd ns xn--mgbbh1a. @8.8.8.8
; <<>> DiG 9.4.2-P2 <<>> +cd ns xn--mgbbh1a. @8.8.8.8
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 27641
;; flags: qr rd ra cd; QUERY: 1, ANSWER: 6, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;xn--mgbbh1a. IN NS
;; ANSWER SECTION:
xn--mgbbh1a. 21599 IN NS ns2.registry.in.
xn--mgbbh1a. 21599 IN NS ns3.registry.in.
xn--mgbbh1a. 21599 IN NS ns6.registry.in.
xn--mgbbh1a. 21599 IN NS ns4.registry.in.
xn--mgbbh1a. 21599 IN NS ns5.registry.in.
xn--mgbbh1a. 21599 IN NS ns1.registry.in.
;; Query time: 76 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Wed Jan 1 23:16:22 2020
;; MSG SIZE rcvd: 148
Zonemaster
- zonemaster.iis.se saved a report on this DNSSEC outage. There's a copy provided by archive.is.
- zonemaster.net also saved a report, while again archive.is saved a copy.
dns.google.com
dns.google.com is related to but seperate from Google Public DNS. During this DNSSEC outage, dns.google.com showed the following for xn--mgbbh1a:
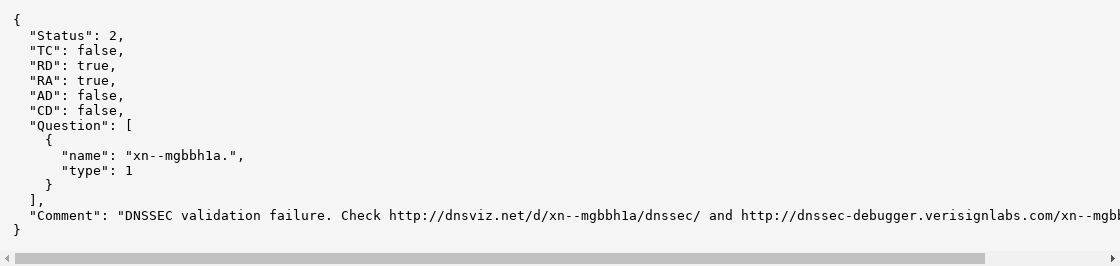
This outage was archived by archive.is.
drill trace
Since DNSSEC contains so much garbage, I put the complete drill trace into its own file, with the relevant portion below (emphasis added):
;; Domain: xn--mgbbh1a.
[B] xn--mgbbh1a. 900 IN DNSKEY 257 3 7 ;{id = 34288 (ksk), size = 2048b}
xn--mgbbh1a. 900 IN DNSKEY 256 3 7 ;{id = 20262 (zsk), size = 1024b}
xn--mgbbh1a. 900 IN DNSKEY 257 3 7 ;{id = 28536 (ksk), size = 2048b}
xn--mgbbh1a. 900 IN DNSKEY 256 3 7 ;{id = 17258 (zsk), size = 1280b}
[B] Error verifying denial of existence for xn--mgbbh1a. type A: No keys with the keytag and algorithm from the RRSIG found
;;[S] self sig OK; [B] bogus; [T] trusted
Logfile examples
These Unbound log entries come from different Unbound instances, each on different servers in different geographical regions.
- [1577920578] unbound[98382:0] info: validation failure <xn--mgbbh1a. NS IN>: signature expired from 37.209.196.12 for key xn--mgbbh1a. while building chain of trust
- [1578402167] unbound[98382:0] info: validation failure <xn--mgbbh1a. NS IN>: signature expired from 156.154.100.20 for key xn--mgbbh1a. while building chain of trust
- [1578402167] unbound[98382:0] info: validation failure <xn--mgbbh1a. NS IN>: signature expired from 156.154.100.20 for key xn--mgbbh1a. while building chain of trust
