.tn TLD DNSSEC Outage: 2019-09-09 to 2019-09-11
Date: September 9 to September 11, 2019
Overview
This page gives some details on the .tn (Tunisia) TLD DNSSEC outage from September 9 to September 11, 2019.
Timeline / DNSViz
(At the time of this writing, DNSViz historical archives have been down for months. DNSSEC makes its users think downtime doesn't matter.)
- 2019-09-09 11:19:15 UTC — first sign at trouble at APEX: NSEC issues
- 2019-09-09 11:27:24 UTC — first <tn. NS IN> DNSSEC failure
- 2019-09-11 15:07:24 UTC — last last witnessed <tn. NS IN> DNSSEC failure
Since DNSViz no longer saves DNSSEC outage info, there is an archive at archive.is.
DNSSEC Debugger
Here's a screenshot of my web browser's output from September 9, 2019:
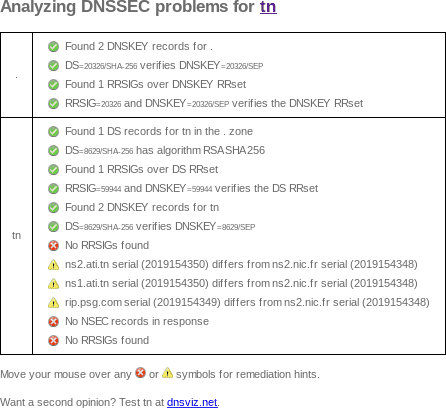
There is a copy of DNSSEC Debugger output saved by archive.is.
Google DNS: with and without DNSSEC
DNSSEC can be disabled in queries via the CD (checking disabled) bit. Let's compare DNS queries with and without DNSSEC.
$ dig +dnssec ns tn. @8.8.8.8
; <<>> DiG 9.4.2-P2 <<>> +dnssec ns tn. @8.8.8.8
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 11270
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 512
;; QUESTION SECTION:
;tn. IN NS
;; Query time: 31 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Mon Sep 9 11:27:27 2019
;; MSG SIZE rcvd: 31
You have to disable DNSSEC to make DNS queries work:
$ dig +cd ns tn. @8.8.8.8
; <<>> DiG 9.4.2-P2 <<>> +cd ns tn. @8.8.8.8
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 299
;; flags: qr rd ra cd; QUERY: 1, ANSWER: 6, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;tn. IN NS
;; ANSWER SECTION:
tn. 21599 IN NS pch.ati.tn.
tn. 21599 IN NS ns1.ati.tn.
tn. 21599 IN NS ns2.ati.tn.
tn. 21599 IN NS ns2.nic.fr.
tn. 21599 IN NS ns-tn.afrinic.net.
tn. 21599 IN NS rip.psg.com.
;; Query time: 18 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Mon Sep 9 11:27:27 2019
;; MSG SIZE rcvd: 158
Zonemaster
- This .tn DNSSEC outage was archived by zonemaster.iis.se
- There is a copy of the above courtesy of archive.is
- There is another copy courtesy of archive.org
drill trace
Since DNSSEC contains so much garbage, I put the complete drill trace into its own file, with the relevant portion below (emphasis added):
;; Domain: tn.
[T] tn. 86400 IN DNSKEY 256 3 8 ;{id = 36171 (zsk), size = 2048b}
tn. 86400 IN DNSKEY 257 3 8 ;{id = 8629 (ksk), size = 2048b}
[U] No data found for: tn. type A
;;[S] self sig OK; [B] bogus; [T] trusted
Since DNSSEC is weird and confusing, the above feels right, but it's wrong. Here is what the output is supposed to look like (the below was taken after the outage):
;; Domain: tn.
[T] tn. 86400 IN DNSKEY 257 3 8 ;{id = 8629 (ksk), size = 2048b}
tn. 86400 IN DNSKEY 256 3 8 ;{id = 36171 (zsk), size = 2048b}
[T] Existence denied: tn. A
;;[S] self sig OK; [B] bogus; [T] trusted
Logfile examples
These Unbound log entries come from different Unbound instances, each on different servers in different geographical regions.
- [1568027955] unbound[31528:0] info: validation failure <isoc.tn. A IN>: no signatures over NSECs from 196.216.168.25 for DS isoc.tn. while building chain of trust
- [1568028444] unbound[31528:0] info: validation failure <tn. NS IN>: no signatures from 204.61.216.94
- [1568036702] unbound[253:0] info: validation failure <tn. NS IN>: no signatures from 147.28.0.39
- [1568214444] unbound[31528:0] info: validation failure <tn. NS IN>: no signatures from 41.228.62.63
- [1568209063] unbound[253:0] info: validation failure <tn. NS IN>: no signatures from 41.228.62.63
- [1568230440] unbound[31528:0] info: validation failure <isoc.tn. A IN>: no DNSSEC records from 204.61.216.94 for DS isoc.tn. while building chain of trust
