cdc.gov DNSSEC Outage: 2019-05-02
Date: May 2, 2019
Overview
This page gives some details on the cdc.gov DNSSEC outage on May 2, 2019. The United States Centers for Disease Control and Prevention has a yearly budget of $11 Billion.
Timeline / DNSViz
DNSViz has been down for weeks at the time of this writing. DNSSEC causes its users to not care about downtime, and some may even like it.
- 2019-05-02 19:46:48 UTC — first personally observed cdc.gov DNSSEC failure
- 2019-05-02 21:14:58 UTC — last personally observed cdc.gov DNSSEC failure
DNSSEC Debugger
Unlike DNSViz, Verisign's DNSSEC Debugger doesn't archive results, so here's a screenshot of my web browser's output from May 2, 2019:
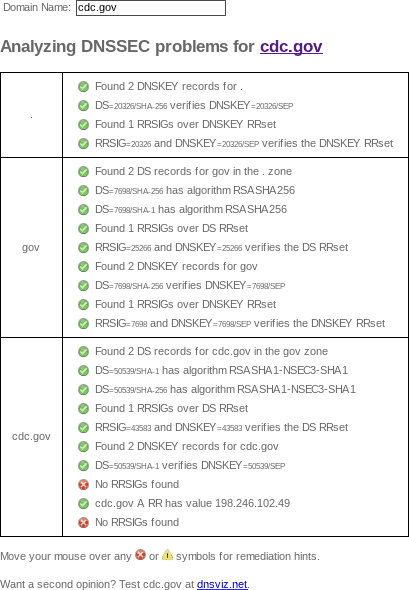
DNS-OARC: BIND
DNSSEC can be disabled in queries via the CD (checking disabled) bit. Let's compare DNS queries with and without DNS SEC.
With DNS-OARC's BIND instance, because of DNSSEC, queries fail:
$ dig +dnssec a www.cdc.gov. @184.105.193.73
; <<>> DiG 9.4.2-P2 <<>> +dnssec a www.cdc.gov. @184.105.193.73
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 29820
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 4096
;; QUESTION SECTION:
;www.cdc.gov. IN A
;; Query time: 3 msec
;; SERVER: 184.105.193.73#53(184.105.193.73)
;; WHEN: Thu May 2 19:47:10 2019
;; MSG SIZE rcvd: 40
You have to disable DNSSEC to make DNS queries work:
$ dig +cd a www.cdc.gov. @184.105.193.73
; <<>> DiG 9.4.2-P2 <<>> +cd a www.cdc.gov. @184.105.193.73
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 58946
;; flags: qr rd ra cd; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;www.cdc.gov. IN A
;; ANSWER SECTION:
www.cdc.gov. 290 IN CNAME www.cdc.gov.edgekey.net.
www.cdc.gov.edgekey.net. 21590 IN CNAME e9313.dscb.akamaiedge.net.
e9313.dscb.akamaiedge.net. 20 IN A 96.16.178.197
;; Query time: 23 msec
;; SERVER: 184.105.193.73#53(184.105.193.73)
;; WHEN: Thu May 2 19:47:10 2019
;; MSG SIZE rcvd: 121
drill trace
Since DNSSEC contains so much garbage, I put the complete drill trace into its own file, with the relevant portion below (emphasis added):
;; Domain: cdc.gov.
[B] cdc.gov. 3600 IN DNSKEY 257 3 7 ;{id = 50539 (ksk), size = 2048b}
cdc.gov. 3600 IN DNSKEY 256 3 7 ;{id = 14768 (zsk), size = 1024b}
[U] cdc.gov. 86400 IN A 198.246.102.49
;;[S] self sig OK; [B] bogus; [T] trusted
Logfile examples
- [1556826408] unbound[10514:0] info: validation failure <www.cdc.gov. A IN>: DS got unsigned CNAME answer from 23.36.2.7 and 23.211.132.65 and 198.6.1.202 for DS www.cdc.gov. while building chain of trust
- [1556826467] unbound[10514:0] info: validation failure <cdc.gov. A IN>: no signatures from 198.246.96.92
- [1556826688] unbound[10514:0] info: validation failure <cdc.gov. A IN>: no signatures from 198.246.96.92 for key cdc.gov. while building chain of trust
- [1556827092] unbound[10514:0] info: validation failure <www.cdc.gov. A IN>: no signatures from 198.246.96.61 for key cdc.gov. while building chain of trust
- [1556831698] unbound[10514:0] info: validation failure <cdc.gov. A IN>: no signatures from 198.246.96.92 for key cdc.gov. while building chain of trust
