dhs.gov DNSSEC Outage: 2018-08-14
Date: August 14, 2018
Overview
This page gives some details on the dhs.gov DNSSEC outage on August 14, 2018. This is the US Department of Homeland Security. dhs.gov gets DNS service from Akamai.
Timeline / DNSViz
- 2018-08-14 02:44:09 UTC — no DNSKEYs
- 2018-08-14 03:02:55 UTC — no DNSKEYs
- 2018-08-14 03:49:31 UTC — no DNSKEYs
- 2018-08-14 04:25:10 UTC — no DNSKEYs
- 2018-08-14 13:13:48 UTC — DNSSEC disabled
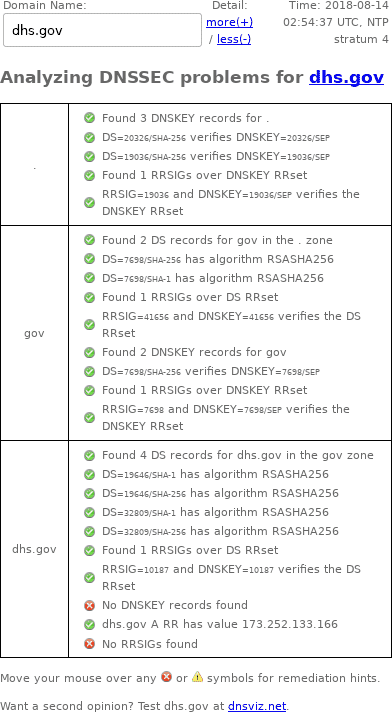
DNSSEC Debugger
Unlike DNSViz, Verisign's DNSSEC Debugger doesn't archive results, so here's a screenshot of my web browser's output from August 14, 2018.
Zonemaster
- zonemaster.labs.nic.cz notes that "No DNSKEYs were returned."
- zonemaster.iis.se also notes that "No DNSKEYs were returned."
Google Public DNS: with and without DNSSEC
DNSSEC can be disabled in queries via the CD (checking disabled) bit. Let's compare DNS queries with and without DNSSEC. With DNSSEC, DNS queries result in SERVFAIL:
$ dig +dnssec a dhs.gov. @8.8.8.8
; <<>> DiG 9.4.2-P2 <<>> +dnssec a dhs.gov. @8.8.8.8
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 34150
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 512
;; QUESTION SECTION:
;dhs.gov. IN A
;; Query time: 16 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Tue Aug 14 03:02:42 2018
;; MSG SIZE rcvd: 36
You have to disable DNSSEC to make DNS queries work:
$ dig +cd a dhs.gov. @8.8.8.8
; <<>> DiG 9.4.2-P2 <<>> +cd a dhs.gov. @8.8.8.8
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 36010
;; flags: qr rd ra cd; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;dhs.gov. IN A
;; ANSWER SECTION:
dhs.gov. 899 IN A 173.252.133.166
;; Query time: 16 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Tue Aug 14 03:02:42 2018
;; MSG SIZE rcvd: 41
drill trace
Since DNSSEC contains so much garbage, I put the complete drill trace into its own file with the relevant portion below (emphasis added):
;; Domain: dhs.gov.
;; No DNSKEY record found for dhs.gov.
[U] dhs.gov. 900 IN A 173.252.133.166
;;[S] self sig OK; [B] bogus; [T] trusted
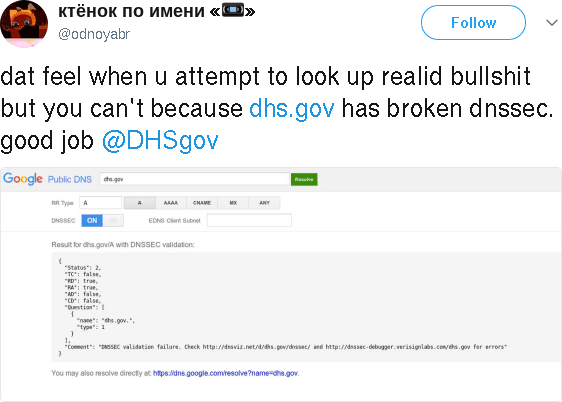
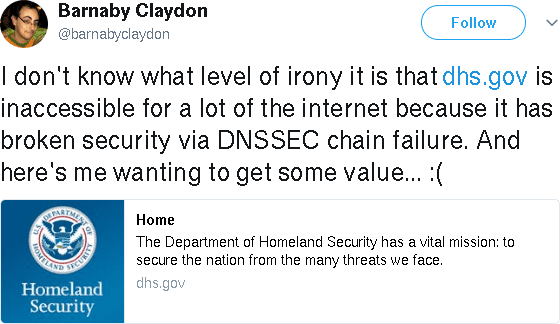
This dhs.gov DNSSEC outage was discussed on Twitter. Here are screenshots in case the posts are lost.
@odnoyabr writes: "dat feel when u attempt to look up realid bullshit but you can't because dhs.gov has broken dnssec. good job @DHSgov"
@barnabyclaydon writes: "I don't know what level of irony it is that dhs.gov is inaccessible for a lot of the internet because it has broken security via DNSSEC chain failure. And here's me wanting to get some value... :(
Logfile examples
- [1534215758] unbound[20292:0] info: validation failure <dhs.gov. A IN>: No DNSKEY record from 184.26.161.65 for key dhs.gov. while building chain of trust
- [1534217354] unbound[20292:0] info: validation failure <dhs.gov. MX IN>: No DNSKEY record from 193.108.91.96 for key dhs.gov. while building chain of trust