dnscrypt.pl DNSSEC Outage: 2017-05-27
Updated: May 28, 2017
Overview
This page gives some details on the dnscrypt.pl DNSSEC outage from May 27 to May 28, 2017. This is a separate DNSSEC outage from the one that occurred a day before.
Timeline / DNSViz
- 2017-05-27 08:26:05 UTC — Bogus DNSSEC delegation
- 2017-05-27 09:20:14 UTC — Bogus DNSSEC delegation
- 2017-05-27 12:27:57 UTC — Bogus DNSSEC delegation
- 2017-05-27 17:59:05 UTC — Bogus DNSSEC delegation
- 2017-05-28 01:59:07 UTC — Bogus DNSSEC delegation
- 2017-05-28 04:19:34 UTC — Bogus DNSSEC delegation
DNSSEC Debugger
Unlike DNSViz, Verisign's DNSSEC Debugger doesn't archive results, so here's a screenshot of my web browser's output from May 28, 2017:
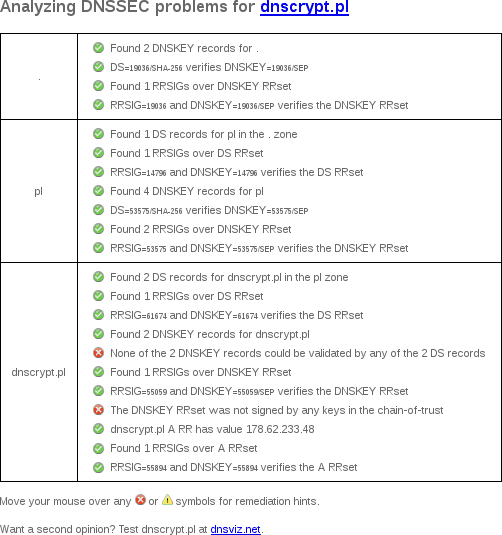
dnscheck
Note: dnscheck requires javascript.
- dnscheck.labs.nic.cz archived this dnscrypt.pl DNSSEC outage, stating "The zone dnscrypt.pl has published DS records, but none of them work."
- dnscheck.iis.se archived this dnscrypt.pl DNSSEC outage, stating "The zone dnscrypt.pl has published DS records, but none of them work."
Zonemaster
- zonemaster.net archived "Delegation from parent to child is not properly signed (no_dnskey)."
- zonemaster.fr archived "Delegation from parent to child is not properly signed (no_dnskey)."
OpenDNS & Google Public DNS
OpenDNS does not support DNSSEC, and instead supports DNSCurve. Google Public DNS currently supports only DNSSEC, and thus, Google's users saw SERVFAIL for queries under dnscrypt.pl during this outage.
With OpenDNS, without DNSSEC, queries succeed:
$ dig www.dnscrypt.pl. @resolver1.opendns.com.
; <<>> DiG 9.4.2-P2 <<>> www.dnscrypt.pl. @resolver1.opendns.com.
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 11291
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;www.dnscrypt.pl. IN A
;; ANSWER SECTION:
www.dnscrypt.pl. 86400 IN A 178.62.233.48
;; Query time: 347 msec
;; SERVER: 208.67.222.222#53(208.67.222.222)
;; WHEN: Sat May 27 08:26:43 2017
;; MSG SIZE rcvd: 49
With Google Public DNS, because of DNSSEC, queries fail:
$ dig +dnssec www.dnscrypt.pl. @8.8.8.8
; <<>> DiG 9.4.2-P2 <<>> +dnssec www.dnscrypt.pl. @8.8.8.8
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 60038
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 512
;; QUESTION SECTION:
;www.dnscrypt.pl. IN A
;; Query time: 336 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Sat May 27 08:26:43 2017
;; MSG SIZE rcvd: 44
Logfile examples
- [1495873536] unbound[23187:0] info: validation failure <www.dnscrypt.pl. A IN>: no keys have a DS with algorithm RSASHA1 from 79.98.145.34 for key dnscrypt.pl. while building chain of trust
- [1495946745] unbound[23187:0] info: validation failure <dnscrypt.pl. MX IN>: no keys have a DS with algorithm RSASHA1 from 193.70.13.218 for key dnscrypt.pl. while building chain of trust
